Managing Team Access to Private Python Packages
Securing private Python packages is crucial for protecting your code and maintaining smooth workflows. Here's how you can manage team access effectively while balancing security and productivity:
- Use Private PyPI Repositories: Host your packages securely with tools like
pypiserverordevpi. Add authentication and enable TLS for secure access. - Leverage Access Tokens: Use token-based authentication for developers and CI/CD pipelines. Rotate tokens regularly and store them securely in tools like AWS Secrets Manager.
- Implement Role-Based Access Control (RBAC): Define roles like Admin, Developer, and Reader with specific permissions to control who can install, publish, or manage packages.
- Integrate with CI/CD Pipelines: Automate secure package installations using environment variables for tokens.
- Review Permissions Regularly: Schedule monthly audits to update roles, remove inactive users, and monitor security logs for suspicious activity.
Quick Tip: Tools like Envelope simplify access control with features like temporary keys, audit logging, and fine-grained permissions.
Key Takeaway: Combine secure authentication, RBAC, and regular reviews to protect your packages without slowing down your team. Ready to dive deeper? Let’s explore the tools and steps in detail.
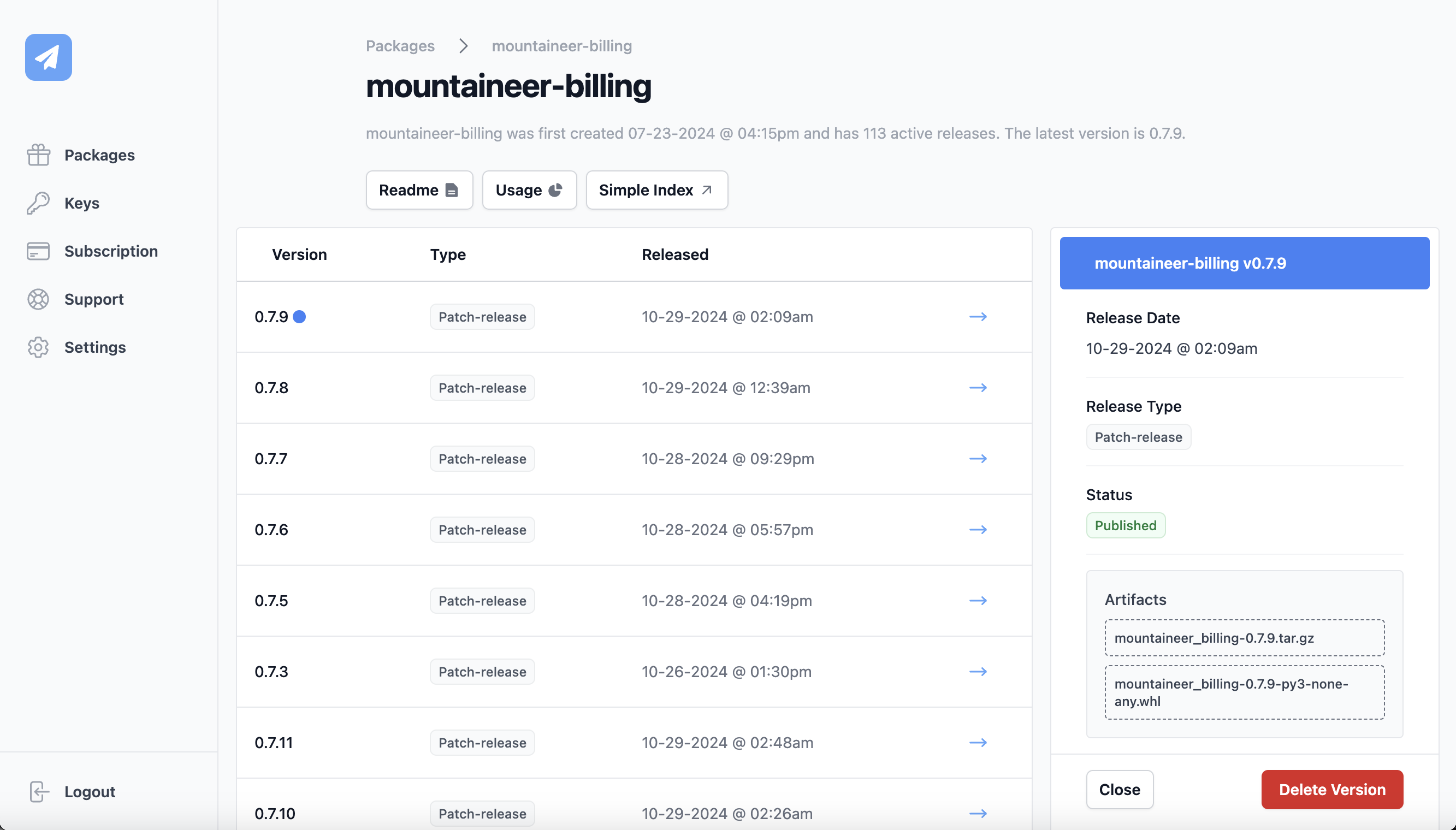
Private PyPi Server
How to Secure Access to Private Python Packages
Protecting private Python packages involves using reliable authentication methods while ensuring developers can work efficiently. Two popular methods are private PyPI repositories and access token authentication.
Setting Up Private PyPI Repositories
Private PyPI repositories allow organizations to host their proprietary Python packages securely. Tools like pypiserver and devpi make it easy to manage packages while sticking to familiar pip workflows.
Here’s how to set up a basic private PyPI repository using pypiserver:
# Install pypiserver
pip install pypiserver passlib
# Create a directory for your packages
mkdir ~/packages
# Start the server with authentication
pypi-server -p 8080 -P htpasswd.txt ~/packages
For added security, it's a good idea to enable TLS encryption to protect your repository traffic.
Using Access Tokens for Authentication
Access tokens simplify authentication by integrating well with existing development platforms. Here are some common token types and their use cases:
| Token Type | Use Case | Rotation Period |
|---|---|---|
| Personal Access | For individual developers | 30-90 days |
| Service Account | For CI/CD pipelines | 180 days |
| Emergency Access | One-time urgent use | After each use |
To implement token-based authentication:
- Generate tokens with the least permissions necessary and store them securely.
- Use tools like HashiCorp Vault or AWS Secrets Manager to automate token rotation and keep systems updated.
In CI/CD pipelines, store tokens in environment variables to ensure secure and automated package installation. For example, a GitHub Actions configuration might look like this:
# Example GitHub Actions setup
jobs:
build:
env:
PRIVATE_PYPI_TOKEN: ${{ secrets.PYPI_TOKEN }}
steps:
- name: Install private packages
run: pip install --index-url https://pypi.internal.org --token $PRIVATE_PYPI_TOKEN
Once access is secured, focus on assigning roles and permissions that fit your team's workflow.
How to Define Roles and Permissions
Role-Based Access Control (RBAC) is a structured approach to managing team access to private Python packages. By assigning specific roles and permissions, organizations can secure their workflows while keeping processes efficient.
Using Role-Based Access Control (RBAC)
RBAC begins with defining roles that align with team responsibilities. Common roles in an RBAC system include:
| Role | Permissions |
|---|---|
| Admin | Full: Publish, modify, delete, manage users |
| Developer | Limited: Install, publish specific packages |
| Reader | Basic: Install only |
| CI/CD Service | Automated: Install during builds |
Here’s an example of how to configure roles for developers and readers using Envelope:
# Example Envelope role configuration
roles:
developer:
permissions:
- install:packages
- publish:team-packages
reader:
permissions:
- install:packages
Adding Permissions to CI/CD Pipelines
To apply RBAC principles in CI/CD pipelines, service accounts with limited permissions are essential. These accounts ensure automated workflows follow the same access rules as team members.
Here’s an example of a simple CI/CD pipeline configuration:
# Example pipeline configuration
steps {
sh 'pip install --index-url https://${PYPI_TOKEN}@pypi.internal.org simple'
}
For better security in CI/CD environments:
- Store tokens securely using environment variables.
- Enable detailed logging for package installations and modifications to monitor any unauthorized activity.
- Automate token rotation for CI/CD service accounts to reduce risks.
When integrating with existing systems, ensure access control remains consistent with your organization’s authentication protocols.
Once roles and permissions are established, you can explore tools like Envelope or custom solutions to simplify private package management.
Tools for Managing Private Python Packages
Handling private Python packages effectively requires tools that prioritize both security and ease of use.
Overview of Envelope
Envelope is a hosted solution, much like Gemfury or Cloudsmith, but it brings features specifically designed for Python developers. It streamlines access control for teams by offering detailed permissions and package-specific keys:
| Feature | Description |
|---|---|
| Fine-grained Permissions | Manage access at both the package and user levels |
| PEP 503 Compliance | Ensures adherence to Python standards |
| Temporary Access Keys | Grant short-term access for contractors |
| Restricted Package Access Keys | Limit access to specific packages |
| Audit Logging | Monitor package usage and changes |
It also integrates smoothly with popular package managers:
# Install packages using pip
pip install --index-url https://app.envelope.dev/simple/ your-private-package
Building Custom Private PyPI Solutions
For organizations that need more control, building a custom private PyPI repository can be a solid option. Tools like pypiserver or devpi allow teams to create tailored solutions with added flexibility and security.
Here are some important factors to consider:
| Factor | Key Considerations |
|---|---|
| Hosting Environment | Decide between on-premises or cloud-based infrastructure |
| Security and Reliability | Choose robust authentication and plan for redundancy |
| CI/CD Integration | Enable automated workflows for package deployment |
More advanced setups may include:
- Centralized authentication using LDAP
- Automated backup and recovery systems
- High-availability configurations for critical environments
- Load balancing to handle large-scale operations
Best Practices for Managing Team Access
Managing team access to private Python packages requires careful planning to ensure security without disrupting collaboration. It's all about keeping your intellectual property safe while making teamwork seamless.
Secure Authentication Methods
The backbone of secure package management is strong authentication. Combining different security layers is the best way to achieve this:
| Authentication Method | Benefits |
|---|---|
| SSH Keys | Offers cryptographic security and can be revoked easily |
| Access Tokens | Simple to rotate and provide precise access control |
| Two-Factor Authentication | Adds an extra security layer to prevent unauthorized access |
While setting up secure authentication is vital, keeping permissions updated over time is just as critical to maintain security.
Regular Permission Reviews
Managing permissions effectively means reviewing them on a regular basis. Focus on these key areas:
| Review Area | Frequency | Actions |
|---|---|---|
| Team Access | Monthly | Check active members, update roles, and remove inactive accounts |
| Security Logs | Weekly | Look for unusual access patterns or suspicious activity |
Platforms like Envelope, designed for managing Python packages, provide built-in tools for auditing. These tools can track:
- Who accessed packages and when
- Trends in user activity
- Authentication attempts
- Token usage data
For larger teams, role-based access control (RBAC) simplifies permission management. For example, you can group users into roles like developers (read-only access) or maintainers (publishing rights).
To make permission management easier and more secure, use tools with built-in auditing and access controls. Envelope's Professional plan, for instance, includes time-limited access keys. These keys automatically expire after a set period, making them perfect for temporary access, such as for contractors or external collaborators. This reduces the risk of forgotten or unused credentials being exploited.
Conclusion: Steps for Better Access Management
Effectively managing team access to private Python packages requires a clear plan that prioritizes both security and efficiency. By leveraging authentication methods, RBAC roles, and specialized tools, you can establish a streamlined access management process.
Consider tools like Envelope to simplify package management. It offers detailed permission settings and secure storage options, starting at $5/month.
Here’s a quick breakdown of the key phases:
| Phase | Key Actions |
|---|---|
| Initial Setup | Set up a private PyPI repository and configure access tokens. |
| Access Control | Define RBAC roles and integrate them into CI/CD pipelines. |
| Monitoring | Enable security logs and create regular review schedules. |
These steps help create a secure and role-specific system for package distribution and monitoring.
When setting up access controls, keep these points in mind:
- Use tokens with limited scopes to secure package installations in CI/CD workflows.
- Enable TLS encryption to protect communications with your repository.
- Tools like Envelope provide features such as time-limited keys, which are great for managing temporary access.
Regular maintenance is essential. Schedule monthly reviews and weekly log checks to stay ahead of potential risks. Built-in auditing tools can help you track access patterns and address vulnerabilities before they escalate.
FAQs
Here are clear answers to common questions about managing private Python packages.
How do you set up a private PyPI server?
A private PyPI server allows organizations to securely distribute packages. To set one up, you'll need to configure SSL certificates, enable authentication, and ensure secure HTTPS connections.
Are private PyPI packages possible?
Yes, you can host private packages. While the main PyPI repository (pypi.org) is public, organizations can use private repositories, either self-managed or through cloud services. Here's a quick comparison:
| Aspect | Public PyPI | Private PyPI |
|---|---|---|
| Access | Open to everyone | Restricted by authentication |
| Hosting | pypi.org | Self-hosted or cloud service |
| Security | Basic package signing | Custom security controls |
| Cost | Free | Costs for infrastructure or service |
Some organizations prefer hosting entire private repositories rather than making individual packages private, as it offers more control.
Can an organization have a private PyPI?
Absolutely. Organizations can create private PyPI servers using tools like private-pypi on AWS or managed services. Options like Envelope ($5/month) and Azure Artifacts make this easier with features like advanced security and reduced maintenance needs. These solutions let you control access, authentication, and security without the hassle of managing everything yourself.
Easy, private Python packages.
Stop worrying about authorizing git clones, manual indexes, or expensive solutions. Envelope makes hosting private packages as easy as publishing to pypi.